Cyber attack
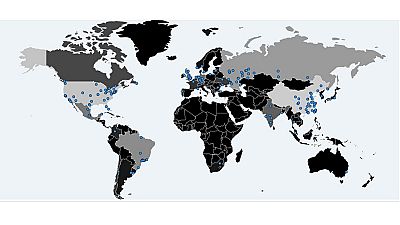
The ransomware WannaCry that infected hundreds of thousands of computers in over 150 countries worldwide since Friday spared a major part of Africa.
The first few hours of the cyber-attack saw major countries and corporations attacked in Europe, the United States, South America and Asia.
Yet, in Africa, the countries attacked were South Africa, Nigeria, Angola, Egypt, Mozambique, Tanzania, Niger, Morocco and Tunisia, according to Kaspersky Lab‘s estimation.
The ransomware takes control of files on Windows computers and demands the payment of $300 dollars in virtual currency Bitcoin before it can restore access or double the cost after three days.
It also threatens to delete the files if payment is not made within seven days.
Ransomware that uses Tor, nice touch. If you were caught out by this its because you left a weaponized RCE vulnerability unpatched. pic.twitter.com/rPFJAGpetp
— Hacker Fantastic (@hackerfantastic) May 12, 2017
Nigeria’s National Information Development Agency (NITDA) said on Sunday that no report of the attack has been recorded in any corporation in the country.
The Director-General of NITDA, Dr Isa Ali Ibrahim Pantami told local media that his agency has some measures in place to stop the spread of the malware; and advised the public to report any abnormal activity on their computers.
Security blog MalwareTech has a map that records the spread of the ransomware. As at Monday, the spread has slowed down with only South Africa in Africa having a few cases.
The spread was reportedly halted after a researcher bought an unregistered website domain that was consistently highlighted during the attack.
Among the institutions affected include UK’s National Health Service organisations, Germany’s rail network, FedEx in the U.S., Renault factories in France and Russia’s interior ministry.
Europe’s cross-border police agency chief Rob Wainwright said the attack was “unprecedented” and they are working with the FBI to identify those behind the malware who are currently unknown.
Microsoft said the attack should serve as a wake-up call after suspicions that the tool used in the attack was stolen from the National Security Agency (NSA) of the U.S.
Microsoft added that it had released a security update in March that could fight the ransomware, and that the affected computers had not been updated.
Experts advise computer users to backup their files, not pay the ransom, install antivirus and update their software’s ransomware removal tools.













Go to video
Paraguayan town celebrates vibrant Kamba Ra'anga festival with masks, fire and tradition
01:47
Chinese city of Xuchang is world's biggest producer of wigs
01:15
U.S. considers adding more African countries to travel ban
01:00
Renewed calls to end plastic pollution on World Environment Day
00:52
Bill Gates says most of his $200 billion fortune will go to Africa over next 20 years
Go to video
Africa’s First Multilingual Small Language Model Gets Even Smaller - Thanks to Top African Innovator